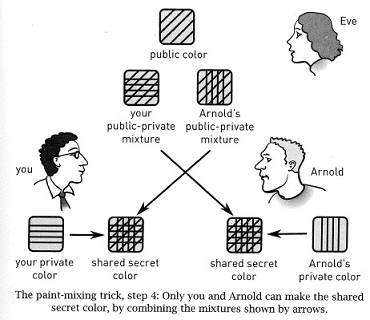
Information sent on the internet is like sending a post card in the U.S. Post --- the postal carriers can read the post card on its way to delivery. For this reason, we need a way of encoding the information written on the ``post card'' so that the ``postal carriers'' cannot read it.
The information on the post card will be encoded using a secret number that is known to only the author of the card (the sender) and the card's receiver.
One way to encode a message is first to rewrite it in its ASCII numbers, a standard computer coding, e.g., A => 65; B => 66; C => 67; etc., and then add the secret number to each numbered letter. E.g., "a cab" is converted to 65 32 67 65 66, where 32 is the ASCII number for a space. If the secret code number is 21, then the encoded message is 86 53 88 86 87.
The previous coding is ``weak'' --- it can be guessed by a smart human. A stronger technique makes the entire message (or each line of the message) into one long number and adds a (very large) secret number to it, e.g., the line "a cab" is converted to the single number, 6532676566, and the secret number, say, 253445763, is added to it, making the encoded message, 6786122329. To decode, just subtract the secret number and convert the ASCII numbers back to letters. (As MacCormick mentions, the coding can be further strengthened by rearranging/inverting the lines, etc.)
The sender of the post card and the receiver must both know the secret number but no one else knows it. But what if the sender and receiver are strangers to each other? How will they both know the same secret number?
Example: Addition is a binary operation. 3 + 2 computes 5. But addition can be undone with subtraction: if we know 5 and that 2 is one of the arguments, we can discover the other argument with addition's inverse operation, subtraction: 5 - 2 equals 3. More precisely,
if x + y = z, then knowing the values of z and x, we can solve for y as y = z - xSo addition cannot be used as the locking operation. Neither can subtraction (why?), multiplication, division, etc.!
For reasons explained a bit later, the unlockable binary math operation requires a commutativity property.
Here's the bad news: no one knows a binary math operation with the commutativity property that cannot be undone. But the good news is, there is a complicated math operation that is a combination of exponentiation and remainders-of-large-prime numbers that no existing computer can undo in years and years. (To make the last phrase more precise, we have to study computational complexity theory, which we may well do by the end of this course!) The exponentiation-remainder operation will work well enough as the locking operation.
We call the exponentiation-remainder operation lockOp. We'll use it like this: starting from a ``public number'' p, we lock up a private number, num, like this:
On Page 57, MacCormick pretends that all humans have forgotten how to do long division by hand (a not-so-far-fetched scenario, alas!), meaning that multiplication can be used as lockOp:
Here is the protocol written out, so that person Sender sends an encrypted message to a stranger, person Receiver. IMPORTANT: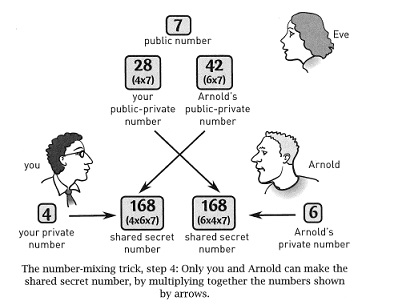
Sender writes the first ``post card'' to Receiver that says, ``Hello, Receiver! I want to use public-key encryption to send you a secret message. Please start with this public number, p.'' The post card is mailed.
Receiver writes the second post card: ``Hello, Sender! I got the public number! Here is my number for you: RPP.'' The post card is mailed.
``Hello, Receiver! I got your number! Here is my number for you: SPP.'' The post card is mailed.
At this point, Receiver knows r and SPP. Receiver computes the secret key as SPP lockOp r. (This equals (p lockOp s lockOp r) which equals (p lockOp r lockOp s).)
When Receiver gets the fourth post card, it decrypts codeMess by subtracting the secret key from it and converting from ASCII back to letters.
Please double-check the above protocol by reviewing the diagram from MacCormick, Page 57.
Next, find a fourth person who remembers how to do both multiplication and long division by hand. Let that person sit with the three people and monitor the communication. Do it again. What happens?
The PostalWorker has inserted itself in the middle of the communication --- the Sender is now communicating with the PostalWorker and the PostalWorker is now communicating with the Receiver. There are two communications going on; the PostalWorker is a participant in both; the Sender and Receiver are clueless. This is known as the ''man in the middle'' attack.
Discuss how the U.S. Postal Service can prevent this attack. How might this strategy be adapted to computer routers?
Example: 24 is 2 * 2 * 2 * 2 = 16.
Example: 14 mod 3 is 2, because one can extract 3 parts of 4 from 14, leaving a leftover of 2. That is, 14 = (3 * 4) + 2; that is, 14/3 = 4 with remainder of 2; that is, 14 - 3 - 3 - 3 - 3 = 2.
In contrast, modulo does not have an inverse operation. For example, if 2 is the answer for n mod 3, the best we can say is that n is one of 2,5,8,11,....
Recall this technical requirement of lockOp, a form of commutativity: For integer arguments x,y,z:
(x lockOp y) lockOp z = (x lockOp z) lockOp yThis requirement is needed so that the Sender and Receiver can compute the same shared secret key.
Hellman and Diffie build lockOp to meet the requirement. Let Clock be a preselected number that defines the range of remainder answers. (E.g., if Clock is 3, then the possible answers are 0, 1, 2.) For technical reasons, Clock should be a prime number. (The definition of prime is at the end of this page.)
Define x lockOp y = (xy) mod ClockOnce you study some group theory, you will be able to prove that lockOp satisfies the commutativity requirement. Further, there is no way to undo (easily!) lockOp:
Say that we already know integers x and SPP, and SPP has locked inside it an unknown integer, y, which we want to know. That is, SPP = x lockOP y. Since SPP = (xy) mod Clock, we deduce that
Solving for both y and d is tough. One must grind out all possible values for d = 0,1,2,... and for y = 0,1,2,... and keep checking the repeated multiplications and subtractions until an answer is found. As MacCormick notes, real-life von-Neumann-based computer architectures, regardless of processor speed or parallellism, cannot finish this for years and years, assuming that the value of Clock is a prime number that is several hundred digits long (that is, over one-thousand bits in length).
(Some bad news: Hellman-Diffie's lockOp operation has the flaw that we only need to try the finite range of values y = 0,1,2,...,(Clock-1) when trying to unlock. The flaw arose because lockOp needs the commutativity property! A good exercise is to study the table on Page 54 and use it to convince yourself of this point.)
There are other locking operations besides this one, but MacCormick chose this one because it is famous and easy to explain.
An easy-to-prove but profound result of number theory is that there are an infinite quantity of primes.
Primes work well for the value of Clock in the definition of lockOp because they force the repeated subtraction that tries to ``unlock'' a number to repeat the maximum times possible, making unlocking almost impossibly hard.
Primes reappear in the next chapter.